With the proliferation of digitization, cloud computing has become a ubiquitous technology, bringing increased efficiency and flexibility to enterprises. As businesses expand, many opt for horizontal scaling of server hosts, which may be distributed across both on-premises and cloud environments. As the number of hosts increases, centralized log management becomes a challenge that every enterprise needs to overcome.
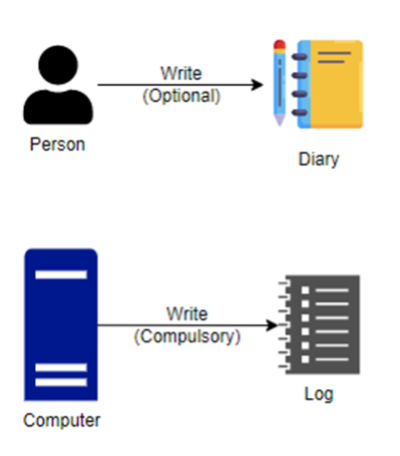
Firstly, let's start by understanding logs. Logs are to computers what diaries are to humans. Let's recall what key content we always include when writing in our diaries! Typically, there's the date and a record of what we did on that date, right? Computer logs are quite similar; they record who (the user) did what at what time.
示意圖
Next, let's take a look at how to find logs on our computers! Here, we'll use the logs of Microsoft Windows 10 operating system as an example. The component responsible for managing log files in Windows operating systems is the Event Viewer. In the Event Viewer, we can see Windows logs organized by events. These logs are categorized into four types:
- Application events: Describes information or error messages from various applications such as drivers and services.
- Security events: Records user activities such as login successes or failures.
- Setup events: Contains information about domain controllers and records installation events of applications.
- System events: Reports problems encountered by the Windows system and services.
Windows Log示意圖
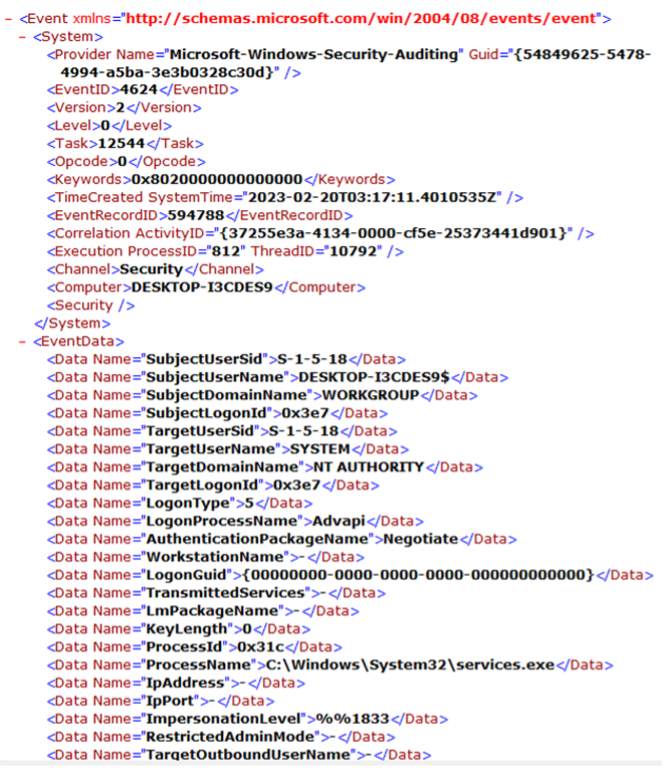
At first glance, a single log entry contains a wealth of information, including fields such as Provider Name, EventID, Version, Task, TimeCreated SystemTime, and so on. Among these, the most crucial field is the EventID (Event ID), represented by <EventID>4624</EventID> in the figure. Simply looking at the number 4624, we may not understand its meaning. To interpret it, we can refer to the common EventIDs shown in the figure. If we need to look up other EventIDs, we can also search for them on the Microsoft website.
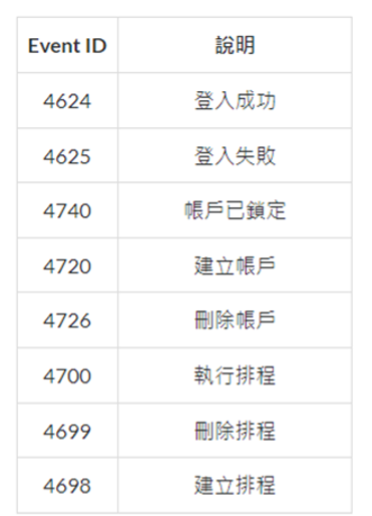
稽核審計中常見的EventID
Now that we have briefly familiarized ourselves with logs and their contents, let's consider what to do if we have to manage many hosts. Join me in the next article, "Building a Trusted Cloud Environment Part Two: Log Solutions," where we'll explore solutions for this scenario.
Solution Architecture
歐律廷 Lambert Ou

