I. Security and Convenience Combined
In the previous issue, we discussed the pain points and concerns faced by enterprises in remote work. We learned that setting up VPN services involves considering many factors, including strengthened passwords, identity verification, server security maintenance, and the load generated by a large number of user connections. These issues could pose serious risks and losses to enterprises, prompting more and more companies to turn to cloud services to address these problems.
Cloud services allow enterprises to avoid building and maintaining VPN services themselves, thus saving costs and time. They also offer higher security and reliability because they typically use the latest security technologies and protocols to protect data and user privacy. Cloud services make it easier for enterprises to expand their remote office capabilities, as they often have good scalability and flexibility to handle changes in user numbers.
- Reducing the threshold for VPN technology setup
- Service maintenance and updates are hosted
- Flexible scalability
- Flexible security level planning and selection
II. New Remote Connection Solutions for Enterprise Cloud
Various cloud service providers have launched corresponding connection security integration services, such as:
Amazon Web Service: Appstream2.0, Workspaces Web Google Cloud Platform: Cloud IAP Microsoft Azure: Azure Bastion These cloud products each have their own advantages. Taking AWS as an example, let's see what features these cloud-native services have to help secure remote connections.
Workspaces Web Workspaces Web is a SaaS fully managed service that does not require the establishment of additional hosts. Users connect via a Web Browser SSL Tunnel encryption and single sign-on IdP authentication. They will then generate a temporary environment for users to use web browsers, suitable for a more secure access to internal web services environments. It is billed based on monthly active users (MAU) and transmitted hourly, allowing for lower costs and more efficient integration and management of users.
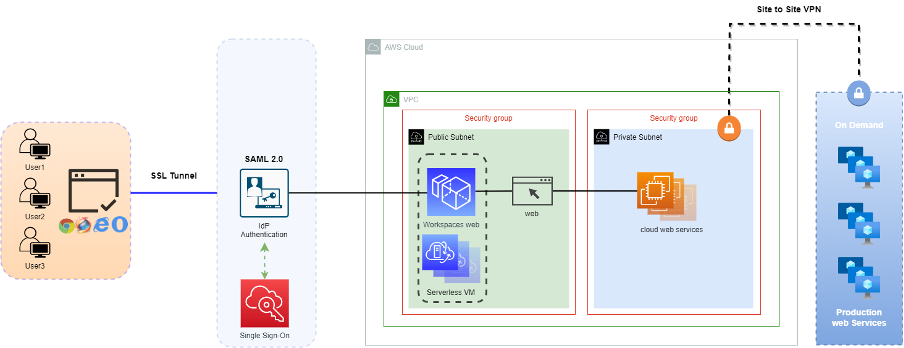
Using Workspaces Web offers several key advantages:
- Default integration of identity verification management through IdP.
- SaaS-level service, fully managed with automatic updates to the latest web browser, eliminating the need to manage host expansion.
- Ensures company data does not reside on remote user devices.
- Provides non-persistent secure access for accessing internal resources and web applications that only require short-term access.
- Isolates users from potentially unsafe environments on the client side.
- Low and predictable costs.
Appstream 2.0 You might wonder, as with Workspaces Web, is IdP authentication the only way to authenticate? What if my service requires remote connections for RDP, SSH, or even database tools? In such cases, Appstream 2.0 can be considered. Users can log in via the Web Console or install the Appstream Client on their devices to connect through an SSL Tunnel encryption. In addition to single sign-on authentication, the service itself provides two types of Active Directory authentication for user identity verification. It also allows for the upload of custom applications, enabling pre-installation of tools expected to be managed during operation and maintenance.
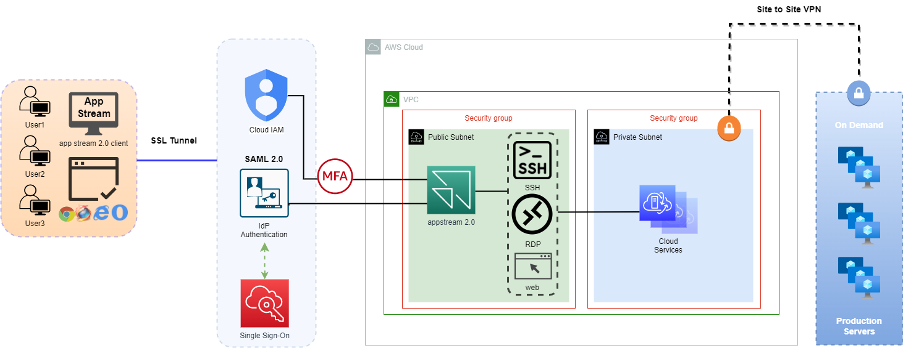
The main advantages of using Appstream 2.0 are as follows:
- Flexible selection of authentication methods.
- Customizable pre-installed management applications.
- Ensures company data does not reside on remote user devices.
- Provides non-persistent secure access for accessing internal resources and applications that only require short-term access.
- Isolates users from potentially unsafe environments on the client side.
- Flexible adjustment of resources and scalability.
Both of these products are fully managed SaaS services, which means we do not need to worry about system vulnerabilities, outdated versions, or server load issues. Depending on the requirements, suitable products can be chosen for the appropriate application scenarios, allowing IT administrators to release themselves from complex security controls. Cloud services offer more flexible choices.
CTO
藍國豪 Levi Lan

